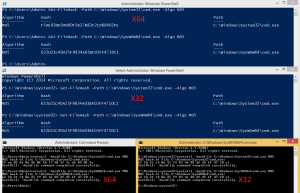
The other day I worked on a little project of mine and accidentally discovered, that Windows is able to produce different hash values for the same input.
wat?!
The problem here is, that the 64bit and 32bit Powershell both create different hash values for the same input, while using build in functionalities like Get-Filehash or binaries like certutil. The behavior is not restricted to Powershell, but expands to CMD aswell.
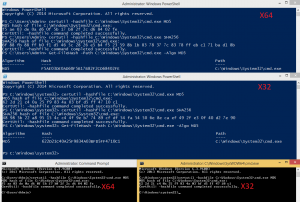
I thought that if somebody actually makes the effort to produce a hash value of something it is usually for something important and not just for fun. Which would mean that it could be important that the hashing algorithm actually works like intended. But when I reported the problem to the the Microsoft Security Center I got the following answer:
What you’re reporting appears to be a bug/product suggestion, but would not meet the bar for security servicing.
So i guess its “not that important”.
Anyway I thought it was nice to know and wanted to share this little story.
UPDATE – 11th May 2020:
To be honest, I was a little dissatisfied with Microsoft’s response. For this reason, I decided to ask people who are absolute experts in the field of IT security in the hope that they could explain to me how the behavior comes about. And I could hardly believe my eyes when Tavis Ormandy took the time to answer my question (which I am very happy and grateful for).
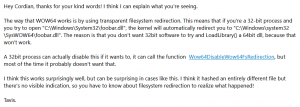
After receiving the email I tried to verify the explanation on one of my machines. I guess my assumption that this was a bug was wrong and that it was more of a feature. A required feature, which, like Tavis himself wrote, delivers a surprising result in this case. Thanks Tavis for the explanation.