Target IP: 10.10.10.247
Box: https://app.hackthebox.eu/machines/Spectra
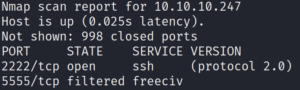
First we run Nmap to detect open ports. As shown in figure one, we are only able to detect two ports with a common “top 1000 ports” scan. One of them being SSH and one of them, which we are most likely not able to identify correct, is actively being filtered.
To make sure 2222 is a normal SSH and not something we identified incorrectly, we pull the banner by performing a script scan.
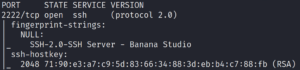
The SSH banner says Banana Studio. Since this is quite uncommon we look for more information on this. A quick Google search tells us, that this is an Android application.
Since we only have port 2222 to access, we run another Nmap scan with the option -p- to identify all open ports of that system.
And indeed we find two more ports on which we run script and version scans against afterwards. Doing so reveals one especially odd looking port.
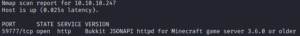
Port 59777 says its a httpd for a Minecraft game server. When we use Google to search for “port 59777” we find that this port is most often used for an ES File Explorer application which is specially used by Android systems. This would make sense since we already saw that the SSH application is from an Android build.
Furthermore Google points us directly at a vulnerability for this service CVE-2019-6447 . Taking a quick look at exploit-db we find an exploit for this.
We download the exploit and run it against the target system. The exploit code seems to work and allows us to list and download files off the target.
We quickly identify something interesting called creds.jpg.
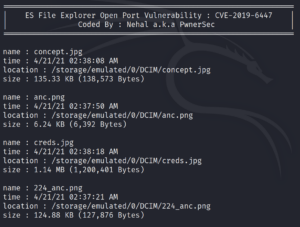
We download the file and take a look at it. The image contains credentials for an user called Kristi as shown in figure 5.
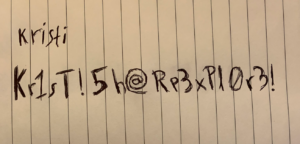
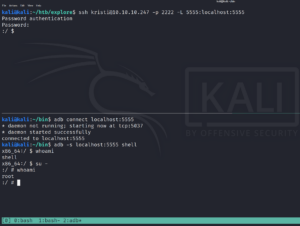
We use these credentials with SSH on port 2222 and we are in. After taking a quick look at the box we remember that there was a port at the beginning that was actively filtered. Lets take a look at it!
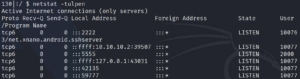
We use Google one more time to search for “android port 5555”. Doing so gives us an article that is about ADB – Android Debug Bridge.
“For the ones not aware of what is ADB, try to think of it as the shell for Android devices, that lets anyone execute commands and install whatsoever they want, thus allowing them to take full control of the device without the need to authenticate. “
Sound pretty much like the thing we are looking for. We install ADB on our attacking Linux machine.
We then create a port forward over SSH from the victim machine to our attacking machine of port 5555. We are then able to use ADB to connect to port 5555 on our attacking localhost machine and access the ADB service of the remote system.
As shown in figure 7, this grants us root access.