Target IP: 10.10.10.229
Attacker IP: 10.10.14.84
Box: https://app.hackthebox.eu/machines/Spectra
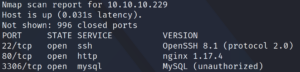
First we start with a Nmap scan as usual. Figure 1 shows that SSH, as well as HTTP and SQL are available.
First we check the web service on port 80 by browsing the website.
From here there are two destinations we can go to, but both redirect to the DNS spectre.htb which is why we need to edit our local hosts file first, if we do not want to replace the name with the IP address for every single webpage we visit.
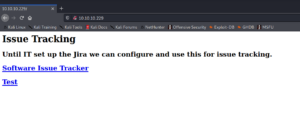
The first site “software issue tracker” goes to a WordPress site as shown in figure 3.
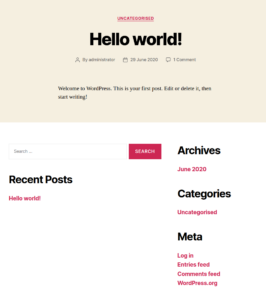
Here find find nothing special – but see a username of one of the WordPress authors called administrator. In the background we can start a wp-scan but we wont find anything useful.
The second website labeled “Test” shows an error message of a DB connection.
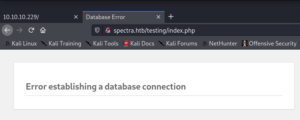
By editing the path and browsing the /testing/ directory we can see a directory listing of a WordPress installation.
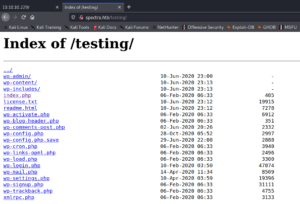
This is interesting since it contains the wp-config.php file, which if we try to reach it we get the same database error as in figure 4.
But if we go and open the wp-config.php.save file we are getting a blank page.
Displaying the page source code shows the PHP code of that file, which contains the WordPress DB credentials.
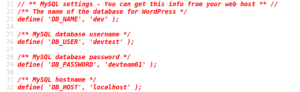
We are not allowed to make any connections directly to the database itself – but due to credential reuse we are able to connect to the WordPress backend with the previously found username administrator and the password devteam01.
Inside the backend we can open the “Theme Editor” tab and we are able to edit any WordPress theme site and sneak in some reverse shell code. For example the 404 template page for theme twenty seventeen as shown in figure 7.
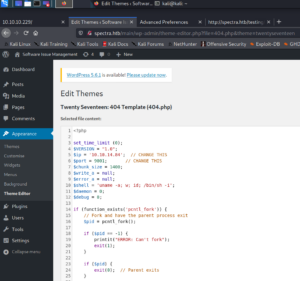
By browsing the template located at http://spectra.htb/main/wp-content/themes/twentyseventeen/404.php we are able to trigger the execution of the PHP code to get shell access to the system.
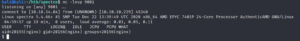
The target machine is running Chromium OS – most likely being a ChromeBook.
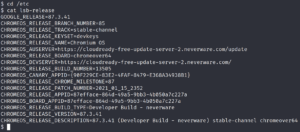
Digging through the machine we find something interesting called autologin inside the /etc/ directory. Inside /etc/autologin/passwd we find a password
which seems to belong to a user account.
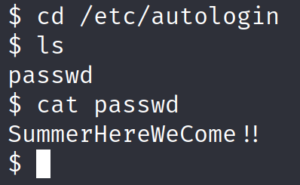
We enumerate the users of the system by taking a look inside the /etc/passwd file and then try to connect to the system over SSH.
After connecting to the target system as user Katie we see that we are able to execute a program called initctl without providing the root password.
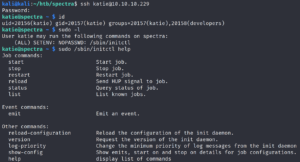
Initctl runs jobs that consist of configuration scripts. Inside the /etc/init/ directory we find that there are some scripts that we are able to edit – since Katie is a member of the developers group as shown in figure 12.
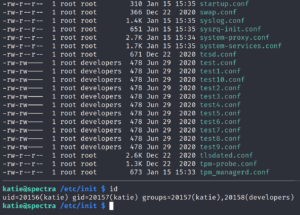
Now, that we are able to edit the content of the test scripts, we place our reverse shell code inside one of the scripts and then use initctl to execute the script as root to receive privileged access to the machine.